AGENDA
- What is Azure Bastion
- How it works
- Key Features
- Architecture
- Conclusion
What is Azure Bastion?
- Azure Bastion is a fully managed solution that allows for more secure and smooth Remote Desktop Protocol (RDP) and Secure Shell Protocol (SSH) access to virtual machines without the use of public IP addresses.
- It is an Azure PaaS solution that allows you to connect to an Azure VM through the browser and delivers safe and easy access directly from the Azure portal.
Azure Bastion secures remote connections by establishing a private virtual network.
Bastion host servers are built and configured to withstand intrusions.
How Azure Bastion works?
Azure Bastion secures the remote connections by establishing a private virtual network that restricts access to remove machines, hence limiting dangers like port scanning and other sorts of malware attacking your VMs.
The deployment of Azure Bastion is done per virtual network, not per subscription/account or virtual machine. When you deploy an Azure Bastion service in your virtual network, the RDP/SSH experience becomes available to all VMs in the same virtual network.
RDP and SSH are two of the most common ways to connect to your workloads operating on Azure.
How Azure Bastion works
Exposing RDP/SSH ports to the Internet is not desirable and is seen as a large danger surface. This is frequently due to protocol flaws.
You can install bastion hosts on the public side of your perimeter network to limit the dangerous surface.
Bastion host servers are built and configured to withstand intrusions.
Key Features
RDP and SSH directly in the Azure portal: You may access RDP and SSH sessions directly in the Azure portal with a single click for a seamless experience.
There is no need for a public IP address on the Azure VM: Azure Bastion establishes an RDP/SSH connection to your Azure virtual machine using the VM’s private IP address. A public IP address is not required for your virtual computer.
Protection against port scanning: Because your virtual computers are not exposed to the public Internet, they are safe from port scanning by rogue and dangerous users situated outside your virtual network.
Remote Session over TLS and firewall traversal for RDP/SSH: Azure Bastion employs an HTML5-based web client that is immediately streamed to your local device, allowing you to connect to your RDP/SSH session over TLS on port 443, allowing you to safely navigate corporate firewalls.
There is no need to worry about NSG management: Azure Bastion is a fully managed platform PaaS solution from Azure.
There is no need to worry about managing NSGs: Azure Bastion is an Azure fully managed platform PaaS solution that has been internally fortified to allow secure RDP/SSH communication.
On the Azure Bastion subnet, no NSGs are required. Because Azure Bastion communicates to your virtual machines using a private IP address, you may configure your NSGs to only accept RDP/SSH from Azure Bastion. This eliminates the need to manage NSGs every time you need to securely connect to your virtual machines.
Protection against port scanning: Because your virtual computers are not exposed to the public Internet, they are safe from port scanning by rogue and dangerous users situated outside your virtual network.
Azure Bastion Architecture
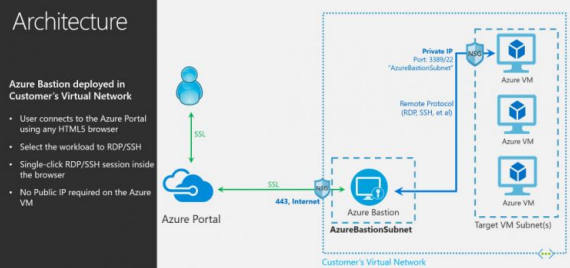
The deployment of Azure Bastion is done per virtual network, not per subscription/account or virtual machine. When you deploy an Azure Bastion service in your virtual network, the RDP/SSH experience becomes available to all VMs in the same virtual network.
RDP and SSH are two of the most common ways to connect to your workloads operating on Azure. Exposing RDP/SSH ports to the Internet is not desirable and is seen as a large danger surface. This is frequently due to protocol flaws. You can limit the danger surface by deploying bastion hosts (also known as jump-servers) on the public side of your perimeter network. Bastion host servers are built and configured to withstand intrusions.
Bastion servers also give RDP and SSH access to workloads behind the bastion and farther into the network.
RDP vs SSH vs Bastian
RDP (Distant Desktop Protocol) is a Windows protocol that allows you to connect to remote Windows virtual machines and servers. RDP necessitates the opening of a port on the remote system, virtual machine, or real server. Because RDP ports are frequently exposed to the Internet and made publicly available, they are frequently targeted by hackers and bots. Companies frequently utilize a virtual private network (VPN) and some type of multi-factor authentication to safeguard RDP instances (MFA).
It is strongly advised not to use RDP without a VPN connection for security concerns. Also, ensure that no RDP sessions are active after you are finished by manually logging off RDP sessions.
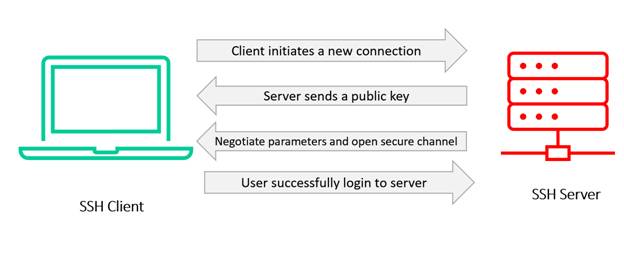
SSH (Secure Shell) protocol, similar to RDP, allows a client system to connect with and send data to another machine (server). SSH has the benefit of protecting communication security and integrity through robust encryption.
In business networks, the SSH protocol is used to provide secure access for individuals and automated operations.
File transfers that are both interactive and automated
Sending out remote instructions
Taking care of network infrastructure and other mission-critical system component
The figure below depicts SSH communication between a client and a server (two computers).
Azure Bastion is a new fully managed PaaS solution that you may deploy within your virtual network. It allows safe and smooth RDP/SSH access to your VMs straight from the Azure site through SSL. Your virtual machines do not require a public IP address when connected using Azure Bastion.